
system
Upgrade to PHP 5.3.3 or newer because of security issue
Thu, 06/09/2011 - 16:26 — Alexis WilkeIf you are responsible for a Debian or Ubuntu server and run PHP on it, make sure to run the following command to fix several security issues found in PHP:
sudo apt-get install php5-suhosin
This will make the necessary and your PHP version (security wise) will look like you have PHP 5.3.3.
What I found quite annoying in regard to this issue is the fact that it was very difficult to find a mention of this upgrade. All I could find in large number were people saying that you'd have to get an upgrade using the source code of PHP. Somehow, I did not feel like upgrading PHP from ...
Protected Node per Node Type Settings
Node Type extension
The Protected Node module adds a field set to the Node Type form that you edit under:
Administer » Content management » Content types
These additions are explained in detail below.
The main reason for adding this feature is to avoid seeing the field set on all the node edit forms. With this feature you can hide the form on all the node types that you will never protect with a password.
Protected mode for nodes of this type
This option let you choose how this node type handles the Protected Node capability.
Never protected
This means this node ...
MobileKey addition to ThemeKey
The main idea of MobileKey is to give you the capability to switch your website theme to a mobile specific theme when the user access your site from one's mobile phone. A mobile theme will make it easier to access your website on a mobile device.
For go to the ThemeKey settings page:
Administer » Site configuration » ThemeKey
The MobileKey adds one selection to the list of attributes to match. The new selection is called:
mobile:device
This works everywhere on your website (it is a global option, not specific to any kind of pages.) The system checks different parameters to
Protected Node Password Form
Protected Node Password Form
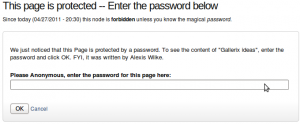 Once a node is protected, users who cannot bypass the password are sent to the password form (see image on the side.)
Once a node is protected, users who cannot bypass the password are sent to the password form (see image on the side.)
The password form is very simple. It includes one field for users to enter the node password and an OK button.
When the browser of the user sent us a referrer, then the Protected node module adds a Cancel link back to that referrer. Using the global settings, you can force a Cancel link to always be there. When no referrer is available, the Cancel link will send your users to your home page.
The title, information, description and title over the
Protected Node Global Settings
The protected node module has global settings found under:
Administer » Site configuration » Protected node
Protected node Statistics
The page starts with statistics to let you know how pages are protected on your website. All the counts include published and unpublished content.
- Total nodes — the total number of nodes on your website
- Unprotected nodes — number of nodes that do not have a password
-
Protected nodes — number of nodes that are current protected by a password
- Showing title — number of nodes showing their ...
IPv4 exhausted!
Tue, 04/12/2011 - 15:11 — Alexis WilkeThat's it! It's official, the IPv4 address space is now exhausted. This happened this year on February 3, 2011. Now what?
Well, first of all the exhaustion was at the level of the IANA, not for each single Internet provider. This means many more IPs are still available.
However, it is important now for everyone to think of writing any new Internet based software so that it works with IPv61
- 1. Remember that if you support IPv6, then your system is capable of accessing all IPv4 addresses since the IPv6 address range includes the IPv4. Now let's hope that the IPv6 is not going to be ...
Insert Node Parameter: override (6-1.3) [special]
WARNING
This parameter is considered a security hazard. There is an option in your format definition that you have to turn on in order for the feature to work. When not selected, override is ignored. Only allow this feature in an input filter where you can trust users 100%.
One can use the override parameter to replace the expected data with their own data. Although one would think using the data directly would work as well, there are cases when this is useful.
By default the InsertNode module gets data from the $node object as defined by the system. At times, the data available in the
Insert Node Parameter: imagefield or imagecache (6-1.3)
The imagefield parameter allows you to insert a CCK image from the specified node.
The parameter must be set to a very specific value for the feature to function properly. The following describes the value:
imagefield=<field name>:<image cache value>:<type>:<index>
The <field name> is the name of the CCK field. You need to include field_ as the introducer. For example, a field you named image is referenced as field_image.
The <image cache value> represents the way the image is displayed. Most often it represents a size such as small, medium, and large.
How to bypass Drupal strong security?
Thu, 02/17/2011 - 16:45 — Alexis WilkeInterestingly enough, today I received a Security Advisory from Drupal saying that users received an email from a hacker asking them to install a Trojan module on their Drupal system.
I find it quite interesting since, if Drupal wasn't secure, the hackers would not have to ask you to make it unsecure, would they?
However, this shows how many CMS systems introduce a security issue problem to your web server installation since it is required to let your web server execute any one PHP file...
All the files installed on your web server and that are directly accessible from the outside (i.e. ...
Similar Modules
To Do Lists
The Todo Filter creates a set of checkboxes on a page that you can click to mark as done. It uses a filter so it can appear in any node that has access to that filter.
The Todolist system that creates a list of To Do items managed using AJAX. Very similar in functionality, but unfortunately not supported anymore.
Advanced Management Systems
The Storm system is an advanced CMS including basic bookkeeping, hours worked, resources. This is not to be used publicly.
