
bad
What kind of test do I need for my software?
Sun, 04/16/2023 - 10:27 — Alexis Wilke
Introduction
Most software companies run in that dilemma. In order to write software that works, you want to write some tests. The question for many of these companies is: what kind of tests are most efficient for my business?
Here we talk about seven common test practices in the software industry.
1. Unit Testing
Probably the most used form of testing is Unit Testing. This is easy to write and very effective in discovering bugs. If you are looking at verifying correctness, this is 100% what you need to have to test your software.
Why is it easy to write?
In most cases, Unit ...
Best way to setup a VirtualBox to avoid system crashes on a reboot
Sat, 03/25/2023 - 09:33 — Alexis Wilke
We now use permanent VirtualBox OSes to run part of our infrastructure.
We ran in all sorts of issues with those, but one thing for sure is that you do not want your OS hard drive to fill up because a (re)boot may not be possible after that. This is because the drive is likely to go bust if completely full.
You should, of course, have tools to let you know how filled up your hard drive is to make sure to catch such issues early. In our case, we had a Jira instance that filled up the drive mainly because we made one backup of the database per day. One day, one of those backup ended that ...
Deleting a (Duplicate) Retweet from your Twitter Feed
Sat, 02/03/2018 - 16:30 — Alexis WilkeDouble Retweeting and How to Avoid Over-Duplication
I have seen many people retweeting like crazy and I've noticed that once in a while these people have been retweeting the exact same tweet more than once.
I'm pretty sure that in most cases these people ignore the fact. Personally I find their twitter feed annoying because of that. Retweeting is totally okay, it's sharing what others have tweeted and there is nothing wrong with it. However, seeing the exact same tweet 2, 3, 4, or even 5 times pretty much in a row is rather bad taste. I understand that this very tweet is super ...
Massive Bug in Intel, AMD, ARM and other Processors in Handling VM Memory
Wed, 01/03/2018 - 14:12 — Alexis WilkeIn the last few days, we started hearing about a massive bug in the implementation of the VM memory handling.
Intel has been frantically working on fixing host machines kernels in order to prevent one VM from accessing the memory of other VMs that run on the same machine.
Of course, most users are not going to attempt to read someone else memory so in that sense, most of us are relatively safe. But all of those who are not so lucky and have uninvited guests on their systems are running at very high risk. The information available from Intel says the memory is accessible only in Read mode. ...
Bad Google Indexing "Secure" Pages...
Wed, 08/22/2012 - 19:45 — Alexis WilkeAbout a week ago I got a customer who started having their website appear in Google with HTTPS (the secure version of the site.) The pages are served securily, but it uses our website certificate so you get a big bad error saying that everything is broken and if you proceed you'll know what hell is like.
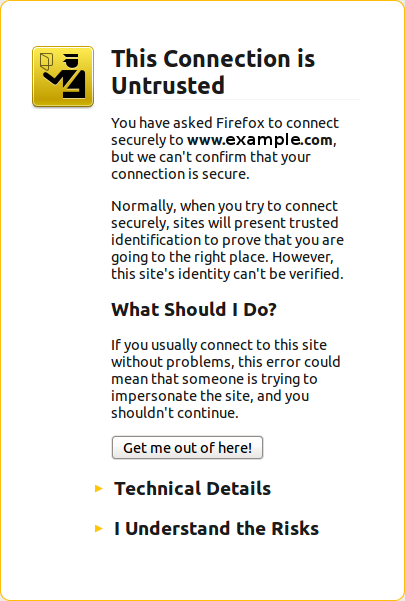 The fact is that this customer never had a secure certificate. In other words, there is no reason for the site to have been referenced with HTTPS unless someone typed a link to their site and inadvertendly entered https://... instead of http://...
The fact is that this customer never had a secure certificate. In other words, there is no reason for the site to have been referenced with HTTPS unless someone typed a link to their site and inadvertendly entered https://... instead of http://...
I checked a few of the pages where there ...
Security Issue in many mail systems
Wed, 07/06/2011 - 12:04 — Alexis WilkeIt always amazes me when one finds a security issue that looks like something that should never have happened in the first place.
This one was found earlier this year by Wietse Venema who first discovered the issue in Postfix.
He fixed the Postfix server quickly, however, he went further. He actually tested many other servers sending commands that bypass that very security measure and to his surprised he found out that Postfix wasn't the only system affected by the problem.
For those interested, all the details of the problem can be found on the Postfix website as CVE-2011-411.
A ...
Drupal Aggregator
The default Aggregator Drupal module does not work very well. There are several problems with the Drupal Core module, one of which we have not fixed in our version (i.e. the flatness of the item table.)
There is a list of the known issues and our comments and whether we fixed the problem:
| Problem | Solution in m2osw's version of Aggregator |
|---|---|
| Missing XML marker | The <?xml ... ?> marker is missing from some RSS feeds, add it as required |
| Spurious data | Some RSS feeds add spurious data ... |
jsMath Security Issue
Security Issue
A security issue was found in all versions of jsMath before 2.x-dev for Drupal 6.x of Jul 29, 2010.
You may still securely use older versions of jsMath on private websites and websites were you are the only user (as in, the only one who can log in.)
The Drupal Security Advisory issue is here: https://www.drupal.org/node/854402
Other Problem
There is another problem: jsMath offers a JavaScript function that parses entire web pages (although there are ways to circumvent that problem, the module does not currently make use of those.) The jsMath Drupal module uses the ...
Cell Phones now open to telemarketers!
Fri, 01/29/2010 - 12:57 — Alexis WilkeThat's it! The phone commissioners have finally decided that it's OK for telemarketers to call cell phones and try to sell you their products and services.
Personally, I do not think that, in itself, it is a bad thing... except that if I receive even just 1 call a day and have to spend 1 minute each time, I will be burning 30 minutes a month for nothing. (Okay, with 1,000 minutes a month, it wouldn't matter that much, but that's like text messaging... if you receive spam via your phone and you have to pay 20 cents for each spam email you receive, the bill goes up quickly ...
SWF Any Filter (swf_any_filter)
A filter defines how to transform the objects it is attached to. The first byte is the filter type. The data following depend on the type. Because each filter is much different, they are defined in separate structures. You can attach a filter to an object using an ActionScript or the PlaceObject3 tag.
The following describes the different filters available since version 8.
Value Name Version 0 Drop Shadow 8 ...
