
available
Massive Bug in Intel, AMD, ARM and other Processors in Handling VM Memory
Wed, 01/03/2018 - 15:12 — Alexis WilkeIn the last few days, we started hearing about a massive bug in the implementation of the VM memory handling.
Intel has been frantically working on fixing host machines kernels in order to prevent one VM from accessing the memory of other VMs that run on the same machine.
Of course, most users are not going to attempt to read someone else memory so in that sense, most of us are relatively safe. But all of those who are not so lucky and have uninvited guests on their systems are running at very high risk. The information available from Intel says the memory is accessible only in Read mode. ...
Domains For Sale
Once in a while Made to Order Software Corporation has a domains for sale. You will find here the list of such domains when some are available. Click on the links to contact us in regard to such and such domain.
If you have any question in that regard, feel free to contact us.
Protected Node Rules Support
The following features are available only when installing the Rules extension of protected nodes. This extension requires the thrid party Rules extension for Drupal.
Protected Node Rules Conditions
When handling a Node, it is possible to check whether the node is currently protected or locked.
Protected Nodes
A node is said protected when the node was protected by a password using the Protected node module.
Whether the user can view that node is irrevelant in this case. Only the fact that the node requires a password to be viewed is what this condition checks.
Locked Nodes
A ...
Upgrade to PHP 5.3.3 or newer because of security issue
Thu, 06/09/2011 - 17:26 — Alexis WilkeIf you are responsible for a Debian or Ubuntu server and run PHP on it, make sure to run the following command to fix several security issues found in PHP:
sudo apt-get install php5-suhosin
This will make the necessary and your PHP version (security wise) will look like you have PHP 5.3.3.
What I found quite annoying in regard to this issue is the fact that it was very difficult to find a mention of this upgrade. All I could find in large number were people saying that you'd have to get an upgrade using the source code of PHP. Somehow, I did not feel like upgrading PHP from ...
MobileKey Installation
Get the tarball or the zip file of the module from Drupal.org (MobileKey on Drupal).
Go to one of you module folders and extract the file you downloaded.
The default installation folder is sites/all/modules, if you have a multi-site installation and want the module for just a few sites, go to sites/<sitename>/modules instead (create the modules folder if it doesn't exist yet.) It is recommended that you do not install under the top modules folder as this one is reserved for Drupal Core modules.
At that point, go to your Drupal website and go to Administer » Site building ...
Protected Node Password Form
Protected Node Password Form
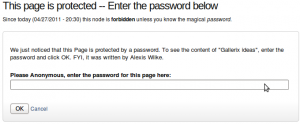 Once a node is protected, users who cannot bypass the password are sent to the password form (see image on the side.)
Once a node is protected, users who cannot bypass the password are sent to the password form (see image on the side.)
The password form is very simple. It includes one field for users to enter the node password and an OK button.
When the browser of the user sent us a referrer, then the Protected node module adds a Cancel link back to that referrer. Using the global settings, you can force a Cancel link to always be there. When no referrer is available, the Cancel link will send your users to your home page.
The title, information, description and title over the
Protected Node Global Settings
The protected node module has global settings found under:
Administer » Site configuration » Protected node
Protected node Statistics
The page starts with statistics to let you know how pages are protected on your website. All the counts include published and unpublished content.
- Total nodes — the total number of nodes on your website
- Unprotected nodes — number of nodes that do not have a password
-
Protected nodes — number of nodes that are current protected by a password
- Showing title — number of nodes showing their ...
To Do Tokens
The To Do module supports tokens that can be retrieved using the Token module.
The available tokens will generally appear in the list of tokens as found under a text area.
The raw tokens are no representing any security risk. They simply return the raw value instead of a more human representation of the value. For example, when the priority is "High", the raw value is 2.
To Do Rules
The To Do module includes a sub-module called To Do Rules extension.
Events
The Rules extension includes the events as follow.
Each event is sent once per user assigned to a To Do item, including self-assigned users. It includes 4 parameters: the To Do item (a node); the To Do item author; the currently logged in user; and the assigned user. The node supports additional tokens that can be used as conditions (see below).
- To Do Event Started
This event occurs when the Start button is clicked on a To Do item. This event is sent once.
- To Do Event Reminder
This event
IPv4 exhausted!
Tue, 04/12/2011 - 16:11 — Alexis WilkeThat's it! It's official, the IPv4 address space is now exhausted. This happened this year on February 3, 2011. Now what?
Well, first of all the exhaustion was at the level of the IANA, not for each single Internet provider. This means many more IPs are still available.
However, it is important now for everyone to think of writing any new Internet based software so that it works with IPv61
- 1. Remember that if you support IPv6, then your system is capable of accessing all IPv4 addresses since the IPv6 address range includes the IPv4. Now let's hope that the IPv6 is not going to be ...
