
address
Reporting a Phishing, Scam, or Abusive email to a financial institution or an Internet company
Sun, 10/05/2025 - 12:44 — Alexis WilkeIn most cases, a large financial institution is going to have an email address where you can send them a copy of a phishing or scam email or website.
I won't get in details about scams in general, I have my Scam Website about that with many emails I've received over the years.
What I like is to have a list of those email addresses because in some cases, it's rather difficult to find them. That way I will have a place for them. You may want to verify before using those email addresses since they may change over time.
| Institution / Company | Scam/Abuse ... |
|---|
Docker, an advanced chroot utility
Fri, 11/29/2019 - 18:09 — Alexis Wilke
SECURITY WARNING
Before installing Docker and containers with services on your Linux system, make sure to read and understand the risks as mentioned on this Docker and iptables page. Especially, Docker will make all your containers visible to the entire world through your Internet connection. This is great if you want to indeed share that service with the rest of the world, it's very dangerous if you are working on that container service since it could have security issues that need patching and such. Docker documents a way to prevent that behavior by adding the following rule to your firewall:
iptables -I DOCKER-USER -i eth0 ! -s 192.168.1.0/24 -j DROP
This means that unless the IP address matches 192.168.1.0/24, the access is refused. The `eth0` interface name should be replaced with the interface name you use as the external ethernet connection. During development, you should always have such a rule.
That has not worked at all for me because my local network includes many other computers on my LAN and this rule blocks them all. So really not a useful idea.
Instead, I created my own entries based on some other characteristics. That includes the following lines in my firewall file:
*filter :DOCKER-USER - [0:0] -A DOCKER-USER -j early_forward -A DOCKER-USER -i eno1 -p tcp -m conntrack --ctorigdstport 80 --ctdir ORIGINAL -j DROP -A DOCKER-USER -i eno1 -p tcp -m conntrack --ctorigdstport 8080 --ctdir ORIGINAL -j DROP -A DOCKER-USER -i eno1 -p tcp -m conntrack --ctorigdstport 8081 --ctdir ORIGINAL -j DROP
My early_forward allows my LAN to continue to work. These are my firewall rules that allow my LAN computers to have their traffic forwarded as expected.
Then I have three rules that block port 80, 8080, and 8081 from Docker.
Docker will add new rules that will appear after (albeit not within the DOCKER-USER list) and will open ports for whatever necessary service you install in your Dockers.
Note that the only ports you have to block are ports that Docker will share and that you have otherwise open on your main server. If Docker opens port 5000 and your firewall does not allow connections to port 5000 from the outside, then you're already safe. On my end I have Apache running so as a result I block quite usual HTTP ports from Docker.
Docker
As we are helping various customers, we encounter new technologies.
In the old days, we used chroot to create a separate environment where you could have your own installation and prevent the software from within that environment access to everything on your computer. This is particularly useful for publicly facing services liek Apache, Bind, etc.
CAPTCHA is not working against all robots anymore but...
Sun, 12/01/2013 - 19:56 — Alexis Wilke
Also many reCAPTCHAs are being bypassed, it still work against many robots, although newer robots use Artificial Intelligence and they are quickly able to bypass most of the reCAPTCHAs.
At some point, the main reason for the bypass was the fact that some people were getting paid to resolve those reCAPTCHAs. In other words, some people were offered the job to do just that! They go to a computer, resolve many reCAPTCHAs and get paid something like 2 cents per successful resolutions. The result is that websites with reCAPTCHAs still receive a lot of spam!
In 2017, it looks like such ...
Protected Node Password Field set
Once installed and properly configured, the Protected node module adds a field set in the node edit form (assuming the user has the corresponding permission: "edit any password" or "edit password <node type>".)
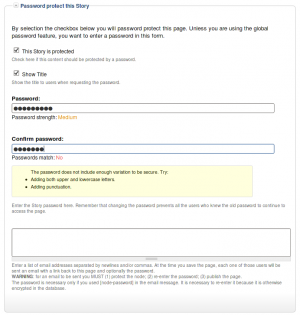 This field set includes two flags, a password, and emails (optional.)
This field set includes two flags, a password, and emails (optional.)
By default, the field set is closed unless you selected protected by default. Whether the field set should be opened or closed can selected in the node type settings.
The <node type> is protected
The first check box is used to password
Protected Node Global Settings
The protected node module has global settings found under:
Administer » Site configuration » Protected node
Protected node Statistics
The page starts with statistics to let you know how pages are protected on your website. All the counts include published and unpublished content.
- Total nodes — the total number of nodes on your website
- Unprotected nodes — number of nodes that do not have a password
-
Protected nodes — number of nodes that are current protected by a password
- Showing title — number of nodes showing their ...
IPv4 exhausted!
Tue, 04/12/2011 - 15:11 — Alexis WilkeThat's it! It's official, the IPv4 address space is now exhausted. This happened this year on February 3, 2011. Now what?
Well, first of all the exhaustion was at the level of the IANA, not for each single Internet provider. This means many more IPs are still available.
However, it is important now for everyone to think of writing any new Internet based software so that it works with IPv61
- 1. Remember that if you support IPv6, then your system is capable of accessing all IPv4 addresses since the IPv6 address range includes the IPv4. Now let's hope that the IPv6 is not going to be ...
Terms & Conditions
Terms and Conditions for the Online Services
offered by Made to Order Software Corporation
This Agreement ("Agreement") is by and between Made to Order Software Corporation ("m2osw") a Californian Corporation and You, your heirs, your agents, successors and assigns ("You" and "Your"), and is made effective as of the date of electronic execution, which is when you register for an electronic account to use the Web site of m2osw. This Agreement sets forth the terms and conditions of Your use of the Online Services ...
Your Privacy
Use of Made to Order Software Corp. website
The following is our policy for the use, by you, of our website. We log a lot of information and we do not have any specific policy in place for when such data will be deleted. Financial related data is kept for a minimum of 10 years.
In all cases, we keep:
- Your IP address and corresponding host name at the time of your connections.
- Your browser information (name, version, computer type, etc.)
- Save cookies in your browser.
- Run JavaScript code on your computer.
- The referrer URL.
- The time and date of all ...
Security Issues with the US government
Wed, 06/11/2008 - 22:23 — Alexis WilkeSome people, I have noticed, have been skeptical about the amount of care taken by the US government and agencies in the last few years. Companies are also catching up. The security measures change every year, when not every semester, every month and for some, probably every day.
For sure, making sure that the most wanted information remains top-secret, you need top level security features on your network. I do not know how much data is of interest, but I found out today that there are hackers attacking the federal websites quite a bit…
“The Pentagon last month acknowledged ...
ANNOUNCING: Online Ordering Seminar featuring Order Made!
Thu, 01/10/2008 - 12:16 — John Codling
Restaurant owners and managers: Please accept our invitation for you to join our seminar on January 22 (1/22) at 11:00 AM. Come and learn about online ordering systems and the importance of having a functional online presence. By functional online presence I mean to have a website that does some of the work for you, whether it be taking reservations or taking orders. And it gets even better - COME FIND OUT WHAT I MEAN!!
You have a website already? GREAT! Plug in the Order Made! online ordering system and start getting a return on your investment. Don’t have a website? Now ...
