
Microsoft
3 Efficient Ways to Store Data Long Term
Tue, 01/17/2023 - 19:13 — Alexis Wilke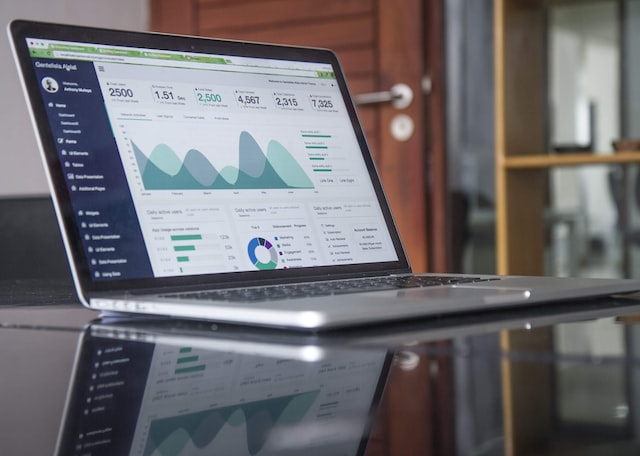 The digital landscape is changing every day. That means that businesses, organizations, and personal information need constant care and attention to maintain their safety, especially if it's data that needs to be kept an eye on for a long time. From being reliable, affordable, and as secure as possible, it's critical that it remains in the right hands.
The digital landscape is changing every day. That means that businesses, organizations, and personal information need constant care and attention to maintain their safety, especially if it's data that needs to be kept an eye on for a long time. From being reliable, affordable, and as secure as possible, it's critical that it remains in the right hands.
This is why we've compiled a list of 3 efficient ways to store data long-term, including using off-site cloud storage plus taking advantage of SQL Server Data Tools. Ready to give your info the safety it deserves? Read on…
Best C++ Books
Tue, 05/07/2019 - 09:21 — Alexis WilkeOnce in a while someone will ask me which book is best to start learning programming. The fact is that I do not know because I'm already an advanced programmer and it's rather difficult for me to get back to the basics (it feels like a waste of my time, sorry...)
That being said, at Made to Order Software, we've mainly been a C++ shop. We also do a lot of C, PHP, JavaScript and touch many other languages as required by the tasks we perform (bash, cmake, perl, C#, Java, etc.)
That being said, I wanted to underline some of the best C++ books available today. Especially, in the last ...
No more excuses! Protect your passwords on your computer with strong encryption.
Wed, 02/14/2018 - 18:05 — Alexis WilkeMore and more, we hear talks about hackers entering personal accounts on systems such as Facebook, Twitter, Instagram and many others. There are many reasons why someone's account will be hacked. One of them is the lack of imagination for their password. Plus, some people use the same password for all of their accounts.
So, if you do it right, you will end up with many passwords. On my end, I have one password per account and that means about 400 passwords... That's totally unmanageable in a fairly standard human brain. For this reason, you end up writing down all your passwords on ...
Massive Bug in Intel, AMD, ARM and other Processors in Handling VM Memory
Wed, 01/03/2018 - 15:12 — Alexis WilkeIn the last few days, we started hearing about a massive bug in the implementation of the VM memory handling.
Intel has been frantically working on fixing host machines kernels in order to prevent one VM from accessing the memory of other VMs that run on the same machine.
Of course, most users are not going to attempt to read someone else memory so in that sense, most of us are relatively safe. But all of those who are not so lucky and have uninvited guests on their systems are running at very high risk. The information available from Intel says the memory is accessible only in Read mode. ...
Snap! Websites
Some of our customers are using the Snap! Websites technology:
We also use it for our websites:
XML Sitemap Setup
The XML Sitemap module allows you to submit your websites to several search engines:
You simply have to turn on the feature and the submissions will automatically happen. To do so, go to admin/settings/xmlsitemap/engines, open each search engine fieldset and select the checkbox, you are done.
Now you probably will notice other fields for the different search engines. Those are used to authenticate your site. It does not make any difference to the submission process. However, it can greatly help you when it ...
odbcpp, a simple C++ library to access ODBC
The ODBC library is an interesting concept created by Microsoft in 1988. It is a library that wraps the implementation details of database managers inside drivers. And these drivers are accessible from the library.
One of the main problem with accessing any database system, is the large number of ...
Your cell phone is hackable...
Fri, 07/31/2009 - 00:02 — Alexis WilkeThis is a quite interesting article which I thought I should share and keep a copy of!
Most of us, even if we can determine whether a piece of software (or hardware!) can be hacked, we just do not have the time to spend on testing each device we use to ensure that no hackers will be able to get it. We rely on the manufacturer to do that work for us.
This article shows that even though all manufacturers have protections, all are vulnerable! And that means your data is vulnerable on your cell phones... Hope this does not scare you too much!
Note by the way that those people who have plenty of ...
Turn Watcher™
 Turn Watcher™ is a Combat Initiative Tracker by Made to Order Software! Turn Watcher was created by gamers for gamers to help you run your combat rounds more smoothly and efficiently.
Turn Watcher™ is a Combat Initiative Tracker by Made to Order Software! Turn Watcher was created by gamers for gamers to help you run your combat rounds more smoothly and efficiently.
Turn Watcher keeps track of the combat order of each player character (PC) and monster involved in your encounters by tracking player and monster initiative order and current hit points so you don't have to!
Turn Watcher lets you make secret skill checks and will saves for player characters. It manages the PCs and monsters that have delayed or readied actions. And it handles automatic bleed out of dying PCs and monsters!
Made to Order Software releases Turn Watcher 1.4 and a new website!
Thu, 12/11/2008 - 01:00 — Doug BarbieriMade to Order Software is proud to announce the release of Turn Watcher version 1.4 and a brand new website!
Turn Watcher version 1.4 incorporates not only some much needed bug fixes (specifically the Stabilize function) but the addition of a brand new feature: Soft Columns.
Use Soft Columns to add, edit and remove rolls and information columns to each of your combatants. For example, you may remove the Spot/Listen columns and replace them with Perception. Add new rolls such as Move Silently and Persuasion. You may also add information-only columns such as Armor Class and Condition Track, ...
